Data protection software includes a wide range of services. In this category you’ll find data management systems, tools for protecting sensitive data, data loss prevention services, vulnerability scanners and threat detection. The ideal data protection package will include all or most of these elements.
The information your organization needs as source material falls into several categories. You have reference data, transactional data and research data. The transactions and research your organization conducts are based on reference data. In the reference data category, you have information about your customers, suppliers, employees, and partners.
Table of Contents
Here Is Our List Of The Eight Best Privacy Software Packages:
The information you have about related companies must be protected because it is likely to be covered by a contractual obligation. For example, a supplier may have given you a customized price list that they don’t want their competitors or other customers to know about. Similarly, your sales team has probably saved the special offers they agreed to in order to win a new customer, and they don’t want their existing customers to know about it. Other important internal business data that needs to be protected is employee salaries and intellectual property.
Reference data in your system that relates to individuals falls under legislation, and you could face fines if this information is shared. The individuals whose data is shared also have the right to sue your company. The laws also govern how you use this data, called personally identifiable information (PII), and even where you store it.
Data Protection Priorities
There are three areas to consider when implementing data protection:
When you set up software to prevent these three types of events, you get a data protection strategy.
In the IT industry, “data loss” usually means data theft. In this guide, we use the term to refer to accidental or environmental events that cause data to become inaccessible. A server damaged by a burst pipe or an IT technician accidentally erasing a hard drive are two examples. In other words, the data is lost and cannot be recovered.
It should be assumed that the only reason you keep the data is because your business needs it to operate. Imagine if all of your system’s client accounts were suddenly deleted, or you lost all of the work in progress that your company’s consultants and engineers saved while working on client accounts.
The consequences of a truly irretrievable data loss would be catastrophic. Not only would the loss of all data of a particular type be catastrophic, but the loss of a portion of the data would be catastrophic. This type of data backup is part of the company’s continuity procedures and relies on backup and recovery systems.
Data disclosure refers to unauthorized access to data. This can occur through theft or sharing. When data is shared among authorized users, it can be accidental or intentional. Intentional disclosure of data may be motivated by resentment of the company, power plays by rival employees, or whistleblowing.
Protecting data from disclosure is done through data loss prevention and threat detection systems.
Data misuse is usually intentional. For example, a company might use the contact information of customers in a department to launch an advertising campaign for the introduction of a new department. Data is kept for a specific purpose and must not be shared for the benefit of unrelated activities. Storing incorrect data is classified as data misuse because it falsely identifies a customer as such. This type of incident can be prevented through data governance and privacy compliance packages.
Since false information is classified as misuse, unauthorized record modification is another form of misuse to guard against. Changes that render stored information inaccurate can be made inadvertently or intentionally by employees, by management to cover up an offense or improve a financial situation, or by an intruder to cover up activities or defame a competitor. This type of data misuse can be prevented by file integrity monitoring (FIM) systems.
The Best Data Protection Software
When looking for the best data protection software, we strive for packages that cover as many of the harmful events that can affect data integrity as possible. Data protection standards such as PCI DSS and HIPAA assume that some data disclosures are unavoidable. In these cases, however, the standards expect organizations to quickly identify the disclosure, loss or corruption of data and notify all individuals affected by the event as soon as possible. The data attacks should also be reported to the appropriate authorities as soon as possible, and remedial action is expected to be taken to recover data or prevent a similar attack.
What Should You Look For In A Data Protection System?
We have studied the market for data backup software and analyzed the options based on the following criteria:
In addition to following these guidelines, we have also looked for tools that cover as many aspects of data protection as possible, as well as specialized systems designed to achieve excellence in specific aspects of data protection.
1. Files.com (FREE TRIAL)
Files.com is a cloud service that acts as a secure file storage and transfer manager. You can improve data protection by centralizing all file storage in one place on this cloud storage system. Uploads to the service are protected by encryption, as the files rest on the server.
Key Features:
Files.com protects data in motion and at rest with AES-256 encryption. This is the strongest encryption system available and is used by the banking industry and the US military. The Files/com system is a data sharing platform that can be used for collaborative file creation via integration with Microsoft 365. It is a secure storage space that can be used for business continuity in the event of an environmental disaster at your location, and is also a good choice as a hub for distributed teams. Store files for distribution and send invitation links for on-site access instead of sending attachments.
Files.com offers you several strategies for data management. You can set up a work practice that requires all files to be created and stored on the cloud platform. This service is integrated with Microsoft 365, so by getting rid of the endpoint software, you’ll have better control over where the files are stored. Each user gets an individual account that lets you track all actions on files. There’s also an administrator account for each plan, with multiple file tracking services built in.
When all files are on the Files.com server, users can distribute or share files by sending a link to the file on the server. Permissions can be restricted to read-only, which controls the number of copies issued for each file and strengthens data protection.
The Files.com system is recommended for any size and type of business. Small businesses save money by not having to buy their own file server, and large companies get unlimited, expandable storage that is secure and can connect distributed teams.
You can try Files.com for free for 7 days.
2. ManageEngine RecoveryManager Plus (FREE TRIAL)
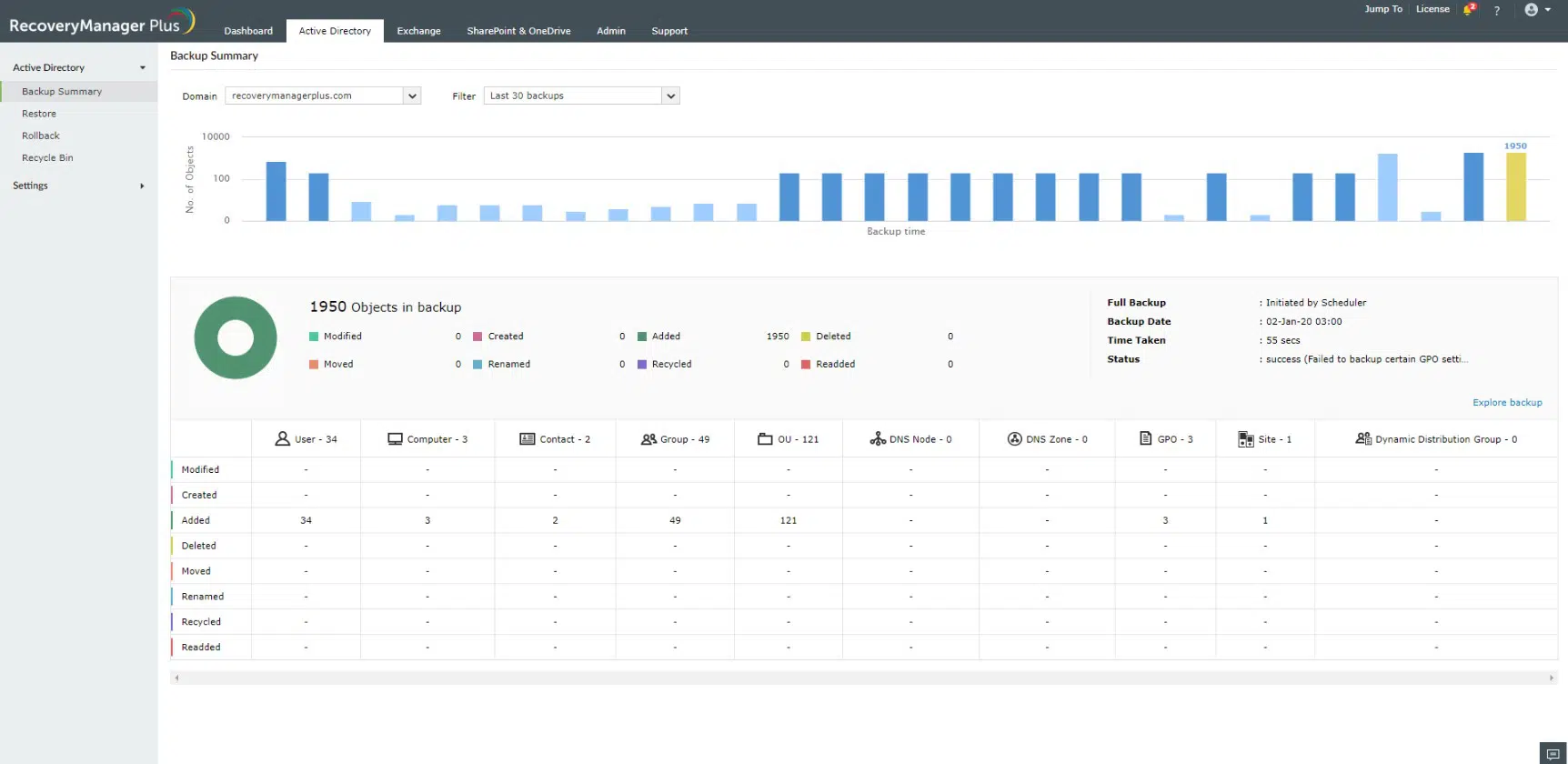
ManageEngine RecoveryManager Plus is a software package for backing up Microsoft systems running on Windows Server or Microsoft SaaS packages, such as Microsoft 365. It can also backup Google Workspace accounts. This tool is especially important for backing up Active Directory and Azure AD.
Key Features:
ManageEngine RecoveryManager Plus is an important purchase for any company that works with Microsoft products. It is especially important for companies that use Active Directory, either on Windows Server or on Azure, for their access rights management system. The service is also great for backing up SaaS packages.
The system not only copies the data from your cloud services, but also backs up the settings for those cloud systems and for Active Directory in its many forms. The service detects changes in your AD instances and copies only those updates, which is a very efficient strategy that puts minimal strain on the network.
The backup and restore system can be run while Microsoft tools are still in use – you don’t have to kick users out of the system to restore data. This is especially important in the case of Active Directory, where a restore might otherwise require booting all users from the system.
Local and cloud synchronization present a complication for backup systems because the same file can exist in multiple locations, and copying all instances wastes space. So, for example, if you sync with OneDrive, back up only the OneDrive system, which automatically takes care of the local copies because the Microsoft service updates the local versions once the files are restored.
Moving and storing data can pose security risks. The ManageEngine system compresses data to save space and protects files with AES-256 encryption, both at rest and in transit. This encryption key is unbreakable and is used by the US military and most banking systems in the world.
Coverage of all AD types – on Windows Server, for Exchange, for SharePoint, etc. – means that replication and SSO systems are coordinated within the backup system. Replication can’t get out of sync, so you don’t have to worry about your data getting corrupted or users being locked out of some of their services due to uncoordinated data recovery in AD.
The ManageEngine system is a good choice for companies that work exclusively with Microsoft, and it also covers Google Workspace, so companies that rely heavily on these cloud systems are the main market for RecoveryManager Plus. Small businesses are attracted to the free version of the package, as it covers all the systems that are also backed up by the paid version, but with some capacity limitations.
ManageEngine gives you complete control over your backup storage strategy, as this element is not included in the package – you have to set up your own storage locations. There is also no choice of which operating system the software runs on, as it is only available for Windows Server. You can try the RecoveryManager Plus system with a free 30-day trial.
3. N-able Cove Data Protection
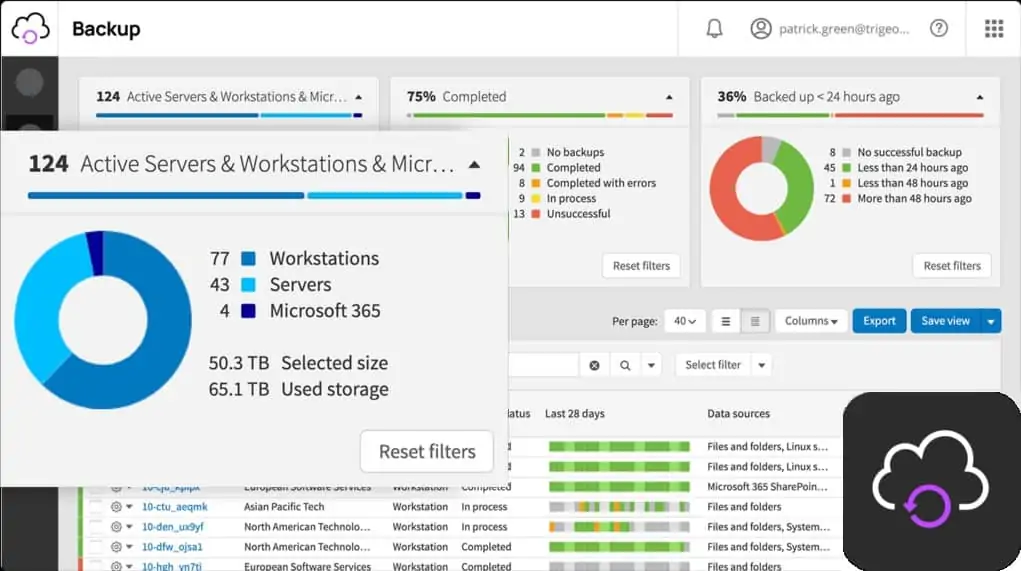
N-able offers a range of services to support managed service providers (MSPs). However, these tools can also be useful for internal IT departments, especially those managing multiple sites. The N-able Cove Data Protection System is cloud-based, so it can automate backup services for any site. The backups created by this system can be used for migration or replication, as well as for restoring lost data to the same location.
Key Features:
N-able Cove Data Protection is a backup and recovery system designed for use by managed service providers (MSPs). The service is one of the tools offered on the N-able platform, all of which are intended for use by MSPs. The central package of this platform is a remote monitoring and management (RMM) package, and Cove Data Protection allows MSPs to add data protection to their regular systems management work. Backup repositories are protected by AES-256 encryption.
Data must be uploaded to the N-able cloud servers for storage. However, this does not pose a security risk as the transfers are protected by strong encryption. This uses the AES cipher with a 256-bit key, which is considered unbreakable. The data is compressed for transmission, which speeds up the storage process and also shortens the recovery phase.
On the N-able server, backups are also protected by 256-bit AES encryption. N-able has data centers around the world and stores your backups at a location closest to your site to shorten transmission distances. The data stored on N-able servers is also mirrored on another server, so there is no risk of losing or damaging the backups you store.
If your business is affected by environmental damage that renders your site unusable, N-able Cove Data Protection allows you to resume operations as soon as you have the alternate site designated in your business continuity plan up and running. The backup system can populate your new servers with your old data, allowing business operations to continue with minimal interruption.
The N-able Cove Data Protection System can manage the contents of both virtual and physical servers. Servers can be backed up to the operating system – even including the operating system. The service has special backup routines for Microsoft Exchange Server, Sharepoint and MySQL. It is also possible to backup OneDrive with N-able Cove Data Protection. Updates can be versioned, creating timed archives that can be used to restore files in whole or in part. This is an important feature for recovering from unauthorized file tampering that may take many backup cycles to discover.
N-able Cove Data Protection has all the storage space you need to store copies of your important data. The backup system is automated and can cover data at any location. The system provides efficiency by constantly running in the background and performing incremental backups. Since it is located off-site, the backup service processes are not affected by environmental damage or system hijacking, which could be the cause of data loss or tampering.
The target audience for Cove Data Protection is MSPs, and the package should be more interesting for existing users of the N-able RMM service. This system would also be suitable for large enterprises with multiple sites.
N-able Cove Data Protection can perform recovery actions on bare-metal servers, physical-to-virtual or virtual-to-virtual. The N-able Cove Data Protection system can be tested during a 30-day free trial.
4. ManageEngine DataSecurity Plus
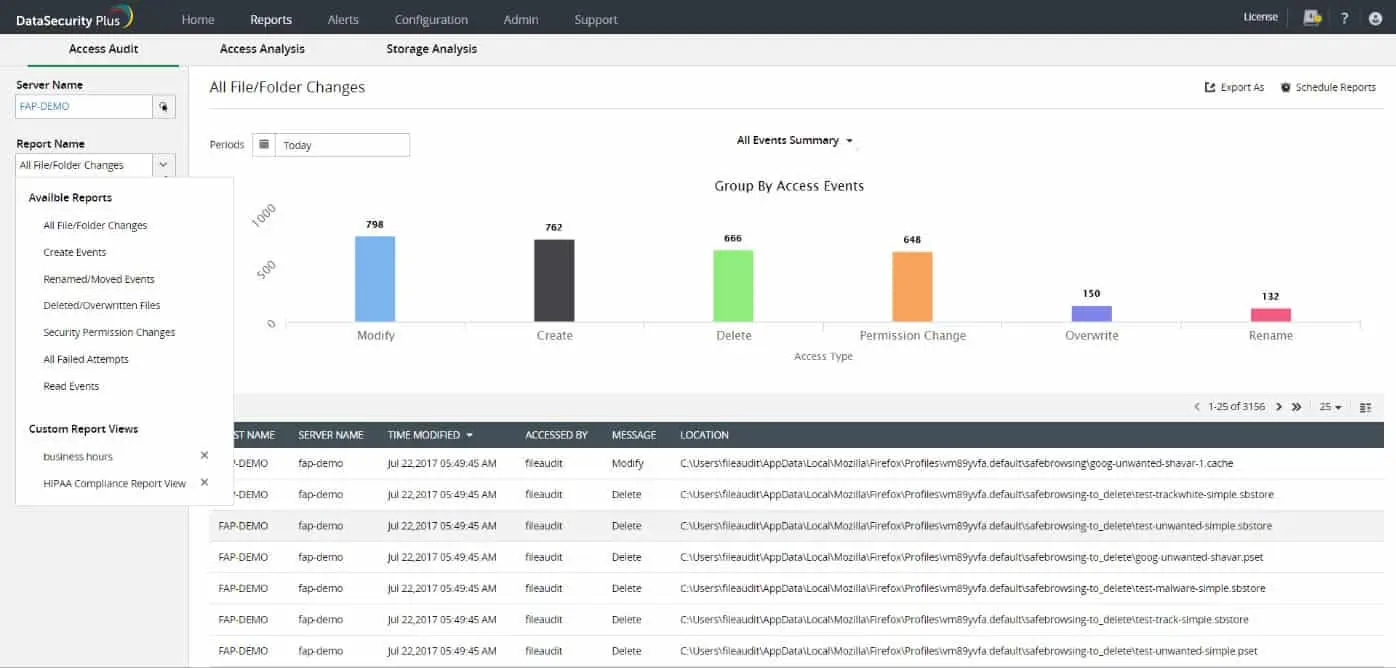
ManageEngine DataSecurity Plus includes File Server Auditing, Data Leak Prevention and Data Risk Assessment. Features of this package include sensitive data detection, data classification, file integrity monitoring, and vulnerability scanning.
Key Features:
ManageEngine DataSecurity Plus is a system for managing sensitive data. It provides a sensitive data detection and classification system that regularly scans your servers for new instances. The service also implements data movement tracking and blocking, including control of peripherals such as USB memory sticks.
The service tracks all your data stores, regardless of whether they are located at one of your sites or on a cloud server. The tool categorizes the data and identifies PII and other sensitive data that requires additional security and tracking. The system analyzes file and access permissions for devices and folders, identifies vulnerabilities and recommends changes.
Other services in the DataSecurity Plus package include File Integrity Monitoring (FIM). This is a tamper protection service that tracks changes to files and records who made those changes and when. This service can be linked to a recovery system to delete unauthorized changes. The service triggers an alarm when a protected file is modified or deleted.
The DataSecurity Plus service monitors USB slots and blocks memory sticks from being plugged in. It is possible to log all file movements on USB drives and selectively block copying of certain files. Similar controls are also available for email attachments.
One feature of the ManageEngine DataSecurity Plus package is that it comes in four separate packages, so you can buy just one or all four. This makes the system more accessible, because if you only need some of the functionality, you won’t have to pay for services you’ll never use. This package is only available for installation on Windows Server.
ManageEngine DataSecurity Plus is an on-premises package that is installed on Windows Server. You can try it free of charge for 30 days.
5. ThreatLocker
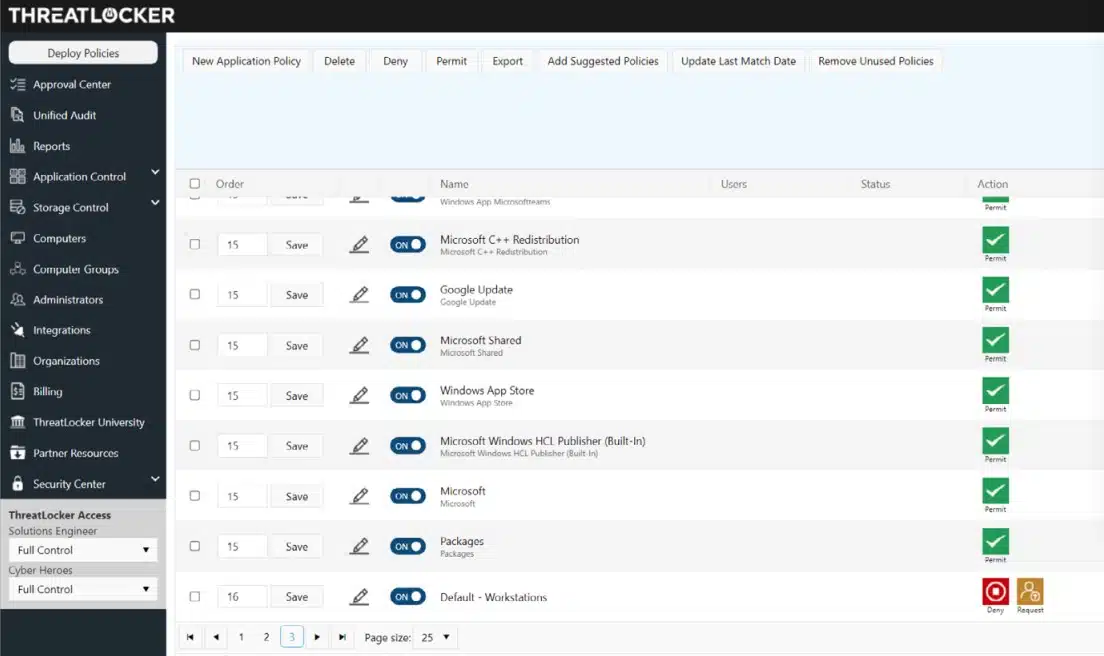
ThreatLocker provides a package of security measures from which a system administrator can assemble a set of protection strategies. With network access control, you can selectively allow access to file servers. Then you can delimit directories or individual files and reserve access to them.
Key Features:
ThreatLocker enables the separation of resources into separate zones with access rights. This strategy is called micro-segmentation and can be applied to resources such as files or to applications. It is also possible to set up activity logging for all data access events, which is required for compliance reporting.
The most important service of the ThreatLocker platform is the Allowlisting package. This automatically blocks all programs running on a protected endpoint. With this software deactivation strategy, ransomware, malware and Trojans are completely blocked from remote access, helping to protect the confidentiality, integrity and availability of your organization’s data.
The system administrator creates a “permission list” and the software in that list is allowed to run. This allows your users to use authorized software, while all other programs cannot run. Further protection of data is achieved through the Application Fencing feature of the ThreatLocker platform. It restricts the resources that an authorized application can access.
You should only use applications that have their own access rights requirements. This provision gets around what is probably the biggest weakness of the ThreatLocker package, which is that it does not include its own access rights manager. You would set up activity logging within the approved application to create audit trails for data protection. This is important for compliance reporting required for PCI DSS, HIPAA and GDPR.
Storage Control is another data protection module in the ThreatLocker platform. This module blocks all USB ports on a protected computer. The system administrator can unblock a port upon request, and access is only allowed to a specific user. All file movements to and from the USB storage device are logged, and the activation of this port can be easily revoked.
The ThreatLocker package is suitable for companies that use both cloud-based SaaS packages and on-premises resources. With this system, you can extend the definition of your network to the Internet and create a virtual network.
With this package, you don’t get detection and classification of personal data. So you already need to know which files or directories need special protection before you create your data protection security policies. You can test ThreatLocker by booking a demo.
6. Trellix Helix
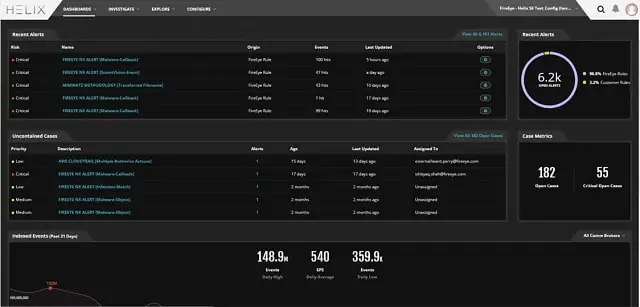
Trellix Helix is a next-generation SIEM service that includes a threat intelligence feed. This service is a good choice to protect your entire IT system and all data from theft or other malicious activities. The service does not only block intruders. It includes a system called User and Entity Behavior Analytics (UEBA), which can detect unusual activity from authorized accounts. This anomalous behavior can indicate a hijacked account or an insider threat.
Account hijacking can be detected by illogical login activity, such as when a user’s account is used in another country. The system tracks the activity of these suspicious accounts, especially in terms of data access.
Key Features:
Trellix Helix is a new name in cybersecurity, but it has a very long history in the field. It is FireEye, which changed its name to Trellix due to a series of splits, mergers and acquisitions. So the company is still establishing its brand, but Trelix already has a solid track record. With this SIEM system, you can protect your data and be sure that threat hunting is up to date thanks to Trellix’s high-quality threat intelligence feed.
You can set up your Helix system to work according to a specific data protection standard. The service works with “playbooks”, which are workflows triggered by a specific combination of events. It is also possible to create your own playbooks. The service is hosted in the cloud, and the dashboard is accessed through any standard web browser. These dashboard screens can also be customized.
Helix is hosted by Trellix on its cloud platform, so anyone can use this package, regardless of operating system. Small businesses will find this package a bit much, but medium and large businesses need the comprehensive threat detection that Trellix offers. It is a general data protection service that does not offer sensitive data detection or compliance reporting.
The integrations in the Helix package exchange data and interact with other applications when you enable them. This makes it easier for the security system to extract activity reports from other services and perform remediation by coordinating with other systems.
7. Acronis Cyber Protect
Acronis Cyber Protect is a bundle of security and data management services. It includes a backup system, a vulnerability scanner and a threat protection system.
Key Features:
Acronis Cyber Protect is a very useful combination of malware protection and backup. It even scans each file before uploading it to the backup repository to prevent your backups from getting infected. Thus, this is the perfect system for ransomware protection. The anti-malware detects the ransomware before it does too much damage. However, it is likely that some files will be encrypted before you notice the infection. However, these files can be deleted from the backup and replaced, so you never have to pay the ransom.
The backup service can also be used to replicate servers so that you can quickly set up new hardware in case your premises are destroyed. This can protect servers running Windows Server and Linux. The backup service works with both virtualizations and physical systems.
Backups can be made to other devices on site or to cloud storage systems. Acronis offers cloud storage, but it is not included in the price of the Cyber Protect system, and the two systems are not connected, so the choice of platform is up to you.
All businesses need anti-malware and backup systems, so getting these two important data protection services in one package is a big time saver when it comes to purchasing. Acronis offers Cyber Protect in different editions suitable for different sizes of businesses, from home offices to multinational organizations.
The controller for the system is in the cloud, and an agent at your location manages all system and data protection services of the Cyber Protect package. Acronis offers this system as a free 30-day trial.
8. Azure Information Protection
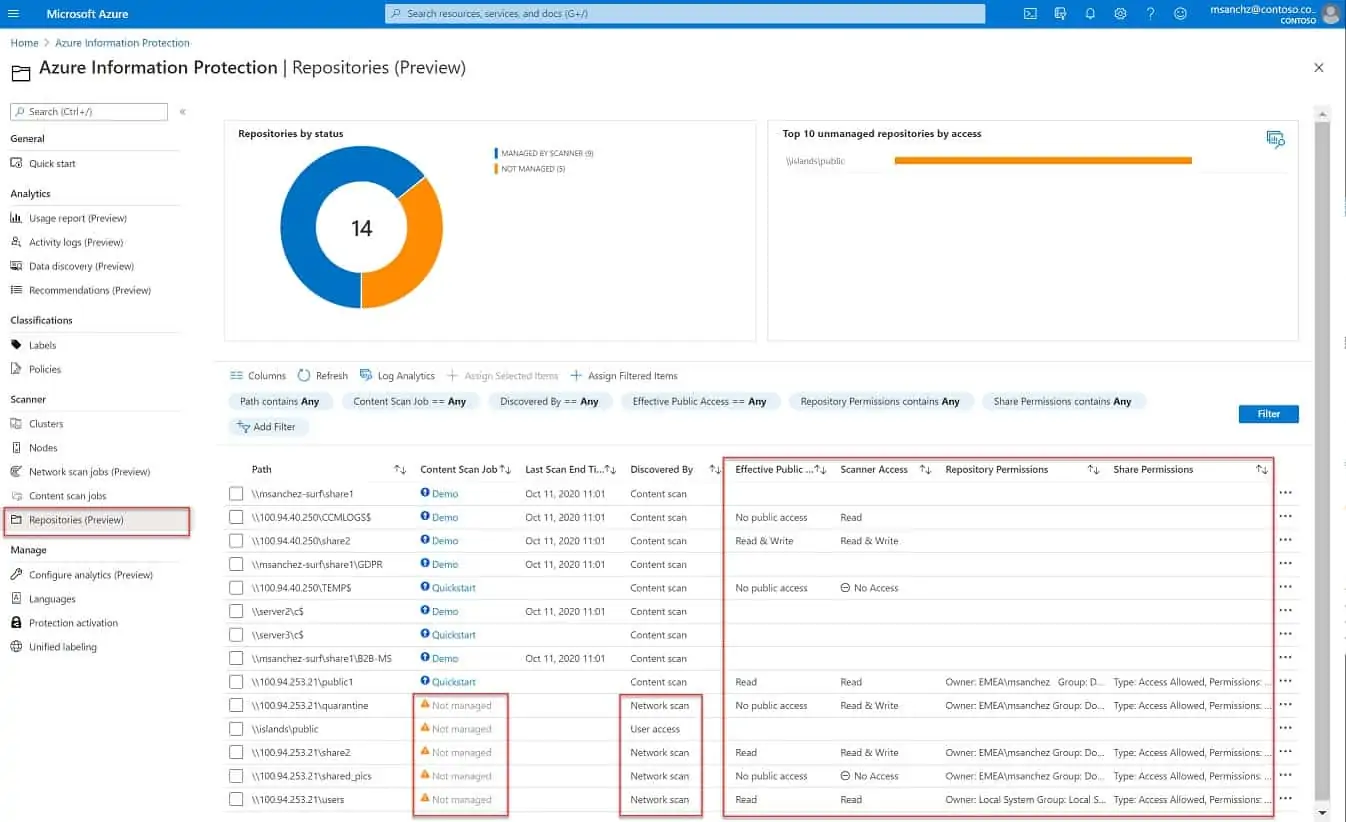
Azure Information Protection scans all your data stores and categorizes the files according to their sensitivity. This action can be applied to any location and also to cloud servers. The cloud data management capabilities are not limited to Azure accounts – the data can be on any cloud platform.
Key Features:
Azure Information Protection is a bundle of data protection services delivered through the Azure platform. Since it is a Microsoft service, it is well integrated with the Azure platform and interacts well with other Microsoft systems, such as Active Directory. However, it is not limited to data residing on the Azure system, so you can deploy it anywhere to protect your data – even on AWS.
The monitoring service works continuously, intercepting new files as they are stored and including them in the classification and control service. The classification of data as sensitive depends on the settings you make in the system. This allows the service to adjust its protection services according to data standards such as GDPR, PCI DSS or HIPAA.
You can prevent sensitive files from being copied or transferred. You can also prevent their content from being printed, and these files cannot be attached to emails.
Azure Information Protection has services that are suitable for many different data management scenarios. For example, it provides data detection and classification for standards compliance and can be aligned with PCI DSS, HIPAA, and GDPR. You also get copy tracking for document distribution through watermarking.
The Azure Information Protection service includes an encryption service to protect files on your server and in transit. You can link the Azure Information Protect service to your Active Directory implementation for access rights management.
Conclusion
Data protection software plays a critical role in safeguarding organizations against cyber threats. The list of top data protection software mentioned above highlights some of the leading solutions available in the market today. Whether it’s the comprehensive features of Files.com, the robust recovery capabilities of ManageEngine RecoveryManager Plus, or the advanced security measures of Acronis Cyber Protect, these tools provide essential protection for data assets.
Additionally, the inclusion of Azure Information Protection underscores the importance of cloud-based solutions in today’s digital landscape. By prioritizing data protection and leveraging these powerful software options, businesses can fortify their defenses and mitigate the risks associated with cyber threats.
FAQs
What is data protection software?
Data protection software is a specialized tool designed to safeguard sensitive information and defend against cyber threats. It employs various techniques such as encryption, access controls, and threat detection to ensure the confidentiality, integrity, and availability of data.
Why do I need data protection software?
In today’s digital age, cyber threats are rampant, and data breaches can have severe consequences. Data protection software acts as a shield, providing an extra layer of security to protect your sensitive information from unauthorized access, theft, and manipulation.
How does data protection software protect my data?
Data protection software uses multiple security measures to safeguard your data. It encrypts your files and communications, making them unreadable to unauthorized individuals. It also enforces access controls, ensuring that only authorized users can access sensitive information. Additionally, it detects and blocks malicious activities, such as malware or hacking attempts, to prevent data breaches.
What types of data can data protection software secure?
Data protection software can secure various types of data, including personal information, financial records, intellectual property, and confidential business data. It can protect data stored on your computer, network, or cloud storage services.
How easy is it to implement data protection software?
Implementing data protection software varies depending on the specific solution. However, many modern data protection software options are designed to be user-friendly, with intuitive interfaces and straightforward installation processes. Some solutions offer seamless integration with existing systems, making the implementation process smoother.
Can data protection software prevent all cyber threats?
While data protection software significantly enhances your cybersecurity posture, it cannot guarantee absolute protection against all cyber threats. It provides robust security measures, but new and evolving threats constantly emerge. Therefore, it is crucial to stay vigilant, keep your software up to date, and follow best security practices to minimize the risks.
To read more similar articles, click here.
Thanks for visiting our Website. If you appreciate our work, kindly show us some support in our comments section. 🙂
Norman Dwemer is a tech blogger who focuses on the future of technology. his blog delves into emerging technologies such as artificial intelligence, blockchain, and quantum computing, as well as their potential impact on our lives and society. Rachel’s writings provide a sneak peek into the future of tech, examining the possibilities and risks of these cutting-edge technologies. he also shares the most recent developments and research in these fields, delivering the latest news and insights to his readers. Norman’s visionary outlook on the world of tech has establihed his as an authoritative figure for anyone interested in the forefront of technology.







